This is one of the most common and effective scams in crypto.
Similar Posts

Is Google Marking Your Site as “Not Secure”? (& How to Fix It)
I know how frustrating it can be when you visit your website and see a big…
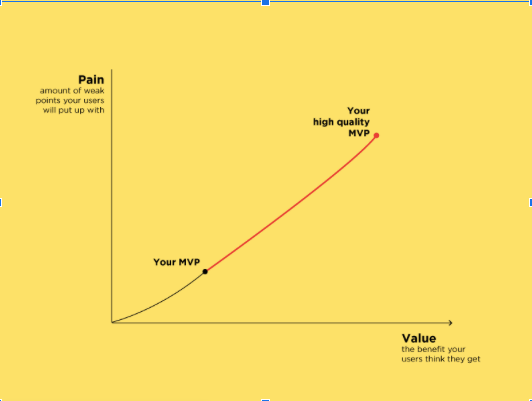
The basics of defining a solid MVP
Any aspiring entrepreneur looking at the success of big tech companies like Facebook, Instagram or Snapchat…

Novacore From India Unveils NVIDIA Blackwell GPU Cloud
Novacore Innovations, headquartered in Mumbai, has announced the deployment of its GPU cloud platform powered by…

AWS Launches European Sovereign Cloud Amid Data Control Push
As concerns continue to mount across Europe about the dominance of U.S.-based cloud providers and the…

Configuring BGP Communities for Custom Traffic in China Routing
Modern enterprises operating across geographical boundaries face a complex web of connectivity, regulatory frameworks, and performance…
Don’t fall for this crypto influencer scam…
Way too many people fall for silly crypto scams like this.